Researchers found a security vulnerability in Microsoft Exchange email server that can be exploited to extract credentials for Windows domains of users around the world.
Detected by Amit Serper, Guardicore’s AVP of Security Research, the bug nests in the Microsoft Exchange’s Autodiscover feature. It is the feature used to configure a user’s email client, such as Microsoft Outlook, with their company’s predefined email settings. If you enter your email address and password to an email client, the server attempts to verify your account to various Exchange Autodiscover URLs. During this verification, the credentials are automatically sent to the Autodiscover URL.
Bugs in this system have caused around 100,000 credentials to be sent to third-party unreliable websites.
This implementation is a crucial part of Exchange email servers as it allows admins to ensure clients use authentic IMAP, SMTP, WebDAV, and other settings. However, to get this done, email clients usually dig a series of pre-established URLs derived from the users’ email address domain. For instance, Serper found the following Autodiscover URLs with the email address ‘amit@example.com:’
- https://Autodiscover.example.com/Autodiscover/Autodiscover.xml
- http://Autodiscover.example.com/Autodiscover/Autodiscover.xml
- https://example.com/Autodiscover/Autodiscover.xml
Microsoft attempting to configure user account via Autodiscover
Exploiting the bug
According to Serper, this Autodiscover protocol used a “back-off” technique when it failed to find the Autodiscover endpoint of the Exchange server in the first attempt. As a result, email clients tried to authenticate to untrusted domains, where all the problems began.
“This “back-off” mechanism is the culprit of this leak because it is always trying to resolve the Autodiscover portion of the domain and it will always try to “fail up” so to speak. Meaning, the result of the next attempt to build an Autodiscover URL would be: http:// Autodiscover.com/Autodiscover/Autodiscover.xml. This means that whoever owns autodicover.com will receive all of the requests that can’t reach the original domain,” explains Amit Serper.
To test his finding, he registered a series of Autodiscover-driven domains that still existed online.
- Autodiscover.com.br – Brazil
- Autodiscover.com.cn – China
- Autodiscover.com.co – Columbia
- Autodiscover.es – Spain
- Autodiscover.fr – France
- Autodiscover.in – India
- Autodiscover.it – Italy
- Autodiscover.sg – Singapore
- Autodiscover.uk – United Kingdom
- Autodiscover.xyz
- Autodiscover.online
The security research company ran honeypots to determine the magnitude of this problem. Turns out, these servers received hundreds of requests from users trying to configure their email clients but could not find their company’s proper Autodiscover endpoint.
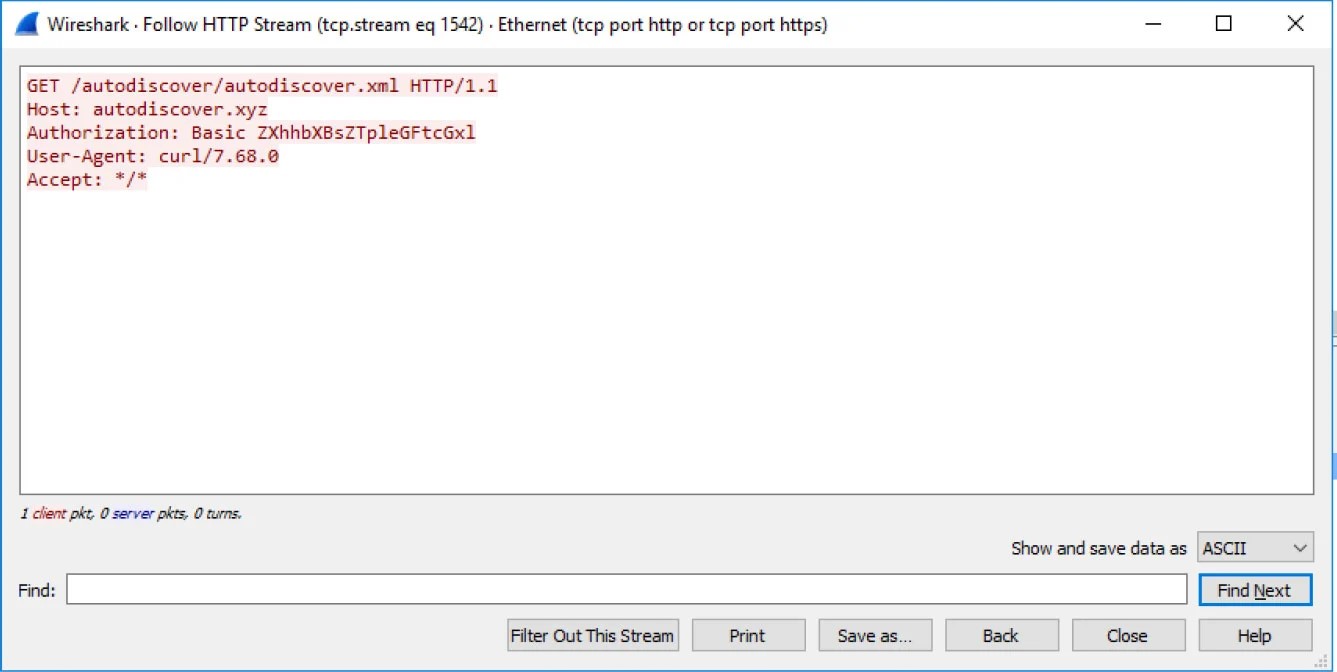
Email client connecting to an autodiscover.xyz URL
“The interesting issue with a large amount of the request that we received was that there was no attempt on the client’s side to check if the resource is available or even exists on the server before sending an authenticated request,” Serper explained in a report published on Wednesday.
“Guardicore has captured 372,072 Windows domain credentials and 96,671 unique credentials from various applications such as Microsoft Outlook,” the researcher said.
While screening the domains connected to the company’s honeypots, he received credentials for companies belonging to different sectors, including:
- Jewelry and Fashion
- Shipping and logistics
- Real estate
- Power delivery and Power plants
- Investment banks
- Food manufacturers
- And Chinese merchandising companies
As per Serper, all the assembled credentials came through unencrypted HTTP basic authentication connections. However, he also detailed how credentials can be harvested from more secure forms of authentication like Oauth and NTLM.
Mitigating the Microsoft Exchange Autodiscover error
To mitigate this error, Serper has provided a few suggestions that organizations and developers can use:
For companies using Microsoft Exchange: Block all Autodiscover.[tld] domains at your DNS, VPN or firewall so your devices won’t be able to connect to them. They are also recommended to deactivate Basic authentications, responsible for sending credentials in cleartext.
For software developers: Serper suggests users to restrict their mail clients from failing upwards while creating Autodiscover URLs to prevent them from connecting to Autodiscover.[tld].
When reached out for comment, Microsoft said:
“We are actively investigating and will take appropriate steps to protect customers. We are committed to coordinate vulnerability disclosure, an industry standard, collaborative approach that reduces the unnecessary risk for customers before issues are made public. Unfortunately, this issue was not reported to us before the research marketing team presented it to the media, so we learned of the claims today.”
