Attention Windows 10 users! Microsoft issued a serious security threat warning, and you need to act!
Microsoft has issued a warning to Windows 10 users that cybercriminals are exploiting a formerly undetected and subsequently unpatched security flaw.
The zero-day hack is a highly critical vulnerability that allows attackers to have complete control over a target’s computer by executing a code remotely. The company itself has confirmed this vulnerability and stated that hackers have already begun exploiting CVE-2021-4044 and urged users to take prompt precautions until the release of an official patch. The U.S Cybersecurity and Infrastructure Security Agency (CISA) also emphasized users “to implement the mitigations and workarounds.”
What is the latest Windows zero-day vulnerability?
The vulnerability plants itself within the rendering engine of the Internet Explorer browser. Wait, Internet Explorer? Seems like we’re safe then, since nobody uses this browser, right? Well, wrong! Not you, but some Microsoft Office documents use this rendering engine, and as a result, providing a clear path to attackers seeking their way into your device!
A researcher at EXPMON detected this vulnerability and reported it to Microsoft on 5th Sept, Sunday. In a tweet posted on Thursday, the security research company warned users to remain “extremely cautious” about files and avoid opening them if not from a trusted source.
Cybercriminals are said to be exploiting the vulnerability via specially-crafted Office documents, -dcx file types, that run MSHTML when opened on a PC. “An attacker could craft a malicious ActiveX control to be used by a Microsoft Office document that hosts the browser rendering engine,” Microsoft explains. Users having no administrator rights will be less affected than those with administrative user rights.
But there’s a catch: Hackers need to persuade users into opening the malicious document for the exploit to work. According to Scott Caveza, a research engineering manager at Tenable, “threat actors are likely to target victim organizations with tailored emails or attempt to exploit current news events for a higher success rate.”
You can check the multiple samples of documents that exploit this vulnerability Here.
Cybercriminals are after the most vulnerable products
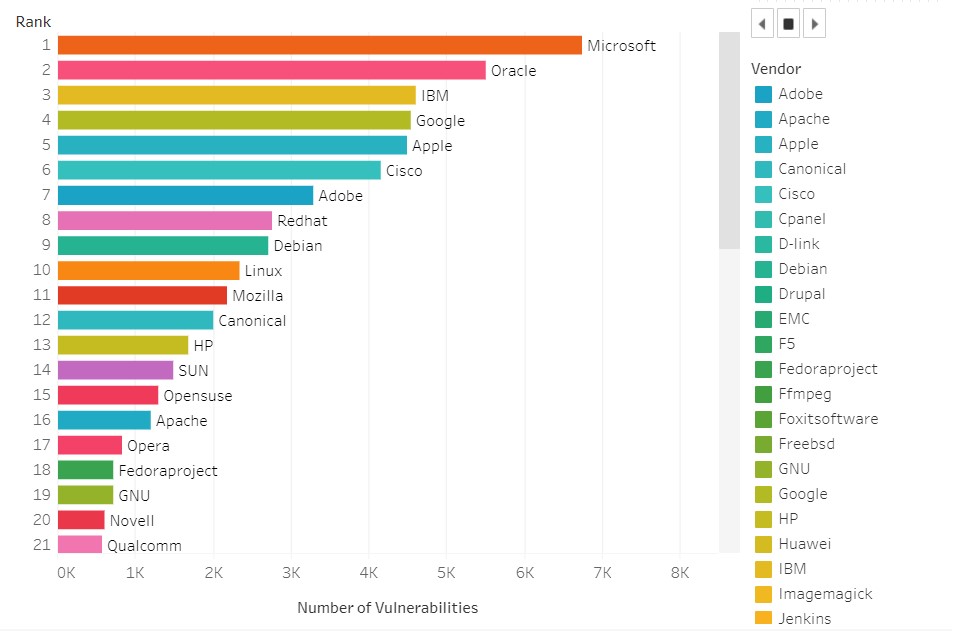
As per the latest CEV details, Microsoft ranks top on the charts for proven security vulnerabilities, with Windows 10 being the most vulnerable Microsoft product. And that explains why hackers are having a field day with zero-day exploits.
“One of the reasons for this spike in zero days is that Microsoft is among the most ubiquitous business software in the world,” said Sam Curry, the chief officer at Cybereason. “If you’re an attacker and want victims, you go after the biggest footprint,” he continued. With Microsoft having the most security vulnerabilities (over 6,700) since 1999, Windows 10 and Microsoft Office certainly is the sitting duck for hackers to take advantage of.
How to prevent yourself from hackers?
It has been established that opening Office documents from untrusted sources is full of risk; hence, it should be avoided. Fortunately, Microsoft defender Antivirus and Microsoft Defender for Endpoint have detection and protections for the vulnerability. If this software is already running on your computer and set to automatic update, you’re safe. However, there is still no specific patch to fix the loophole itself. It’s expected to be released next week as part of the Patch Tuesday cycle, or maybe even earlier as an out-of-band patch update.
For the time being, users are recommended to be extremely cautious about opening Microsoft Office files and implement the workarounds and mitigations that Microsoft has released.
For starters, documents downloaded from the internet are automatically set to open in either Application guard or Protected View for Office. This prevents the infected ActiveX control from gaining control of your device.
To be extra safe, you can disable Internet Explorer ActiveX from being installed on your device in the first place. However, any existing downloaded ActiveX on your PC will continue working, as usual, Microsoft clarifies. The company has also released directions on how to perform that, but it’s worth mentioning that the process involves tempering the Windows registry. If you’re not that tech-savvy, it can cause real headaches if you accidentally change something you shouldn’t suppose to.
So, unless the patch releases, avoid downloading office documents from a suspicious source like an email sent from an unknown sender. To have an extra layer of protection, you can even use a reliable VPN connection to keep your online identity hidden and encrypted.
It’s been a terrible year for Microsoft when it comes to security, especially with zero-day attacks. Many vulnerabilities have been detected in the Windows Print Spooler over the recent months, which could potentially permit hackers to take complete control over a compromised system.