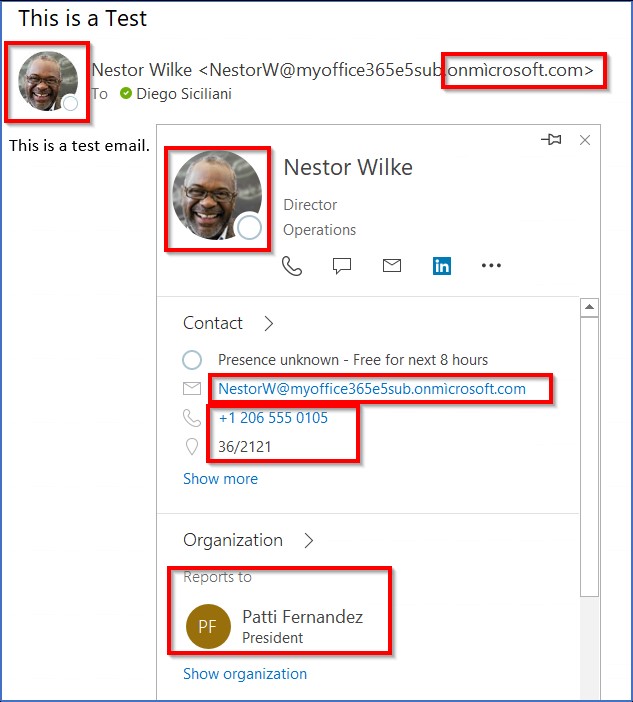
Two security researchers discovered a vulnerability in Microsoft Outlook that enables phishing attacks using internationalized domain names (IDNs). The email service displays an actual contact detail alongside a scam email sent from these domains, making it look real to the recipient.
Phishing emails sent from IDNs are also called homograph attacks. These emails consist of Unicode characters from non-Latin alphabetical sets, such as Greek or Cyrillic, which appear exactly the same as the usual Latin characters. For example, an attacker might register the domain “tωitter.com,” which uses a non-Latin substitute to a regular “w.”
But this isn’t something new. There was a time when modern browsers could not make any apparent distinction between domains with mixed character sets when typed in the address bar. But turns out Microsoft Outlook is still stuck in that age! The email service cannot distinguish between the actual and a lookalike domain, resulting in displaying a legitimate contact card of a real person registered in a real domain.
According to a security researcher dobby1kenobi, Microsoft was unable to detect spoof domains. He writes in his blog post, “I recently discovered a vulnerability that affects the Address Book component of Microsoft Office for Windows that could allow anyone on the internet to spoof contact details of employees within an organization using an external lookalike Internationalized Domain Name (IDN).”
He continued, “This means if a company’s domain is ‘somecompany[.]com’, an attacker that registers an IDN such as ‘somecompany[.]com’ (xn—omecompany-I2i[.}com) could take advantage of this bug and send convincing phishing emails to employees within ‘somecompany.com’ that used Microsoft Outlook for Windows.”
In short, if a spoofed email with an IDN similar to a legitimate email address in the recipient’s Outlook contact book, it will display the actual person’s contact details. And because of it, many employees will be tricked into assuming that the email is legitimate.
Mike Manzotti, a senior consultant at the security firm Dionach, also discovered this issue and reported it to the tech firm. Microsoft released a statement in his response stating, “We have finished going over your case, but in this instance, it was decided that we will not be fixing this vulnerability in the current version and are closing this case,” the company said. “In this case, while spoofing could occur, the sender’s identity cannot be trusted without a digital signature. The changes needed are likely to cause false positives and issues in other ways.”
However, Manzotti did not find any such issue in the latest version of Microsoft Outlook (16.0.14228.20216). Unfortunately, though, the company hasn’t yet confirmed this fix.
Companies using outdated versions of Outlook can deter spoofing attacks by digitally signing their emails and manually filtering all emails from unknown sources. They are also advised to use Virtual Private Network (VPN) for encrypted and secure communication between employees.