Dubbed as “TangleBot,” a new kind of malware has been discovered targeting Android smartphone users in the US and Canada. The hackers are said to be using SMS smishing malware as part of COVID-19 awareness campaigns to trick users into clicking infected links for stealing private and financial information, according to security research analysts at Cloudmark.
“The malware has been given the moniker TangleBot because of its many levels of obfuscation and control over a myriad of entangled device functions, including contacts, SMS and phone capabilities, call logs, internet access, and camera and microphone,” the researchers said.
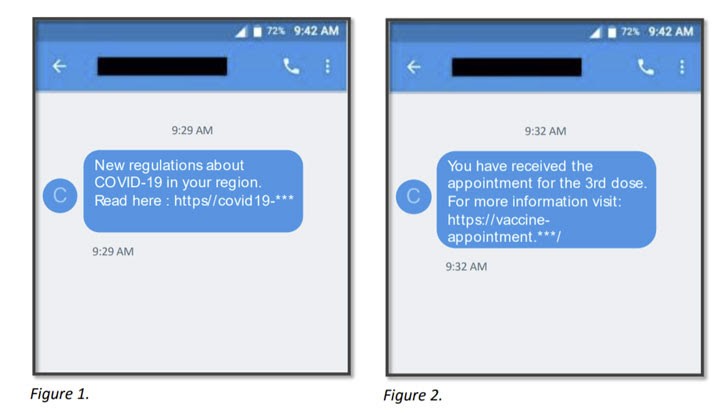
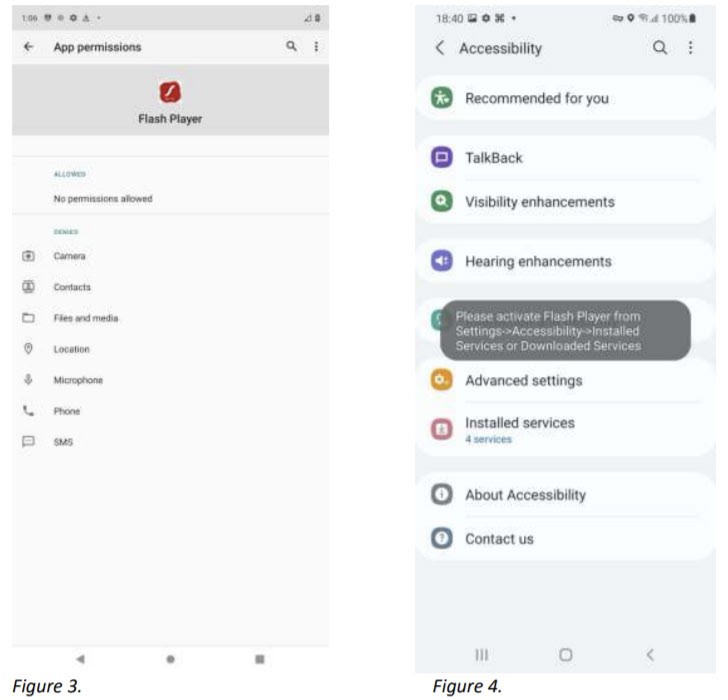
This malware sends a text message to Android users, claiming to carry the latest COVID-19 related information or the appointment details of the third Covid-19 vaccination. Upon clicking on their provided links, you will be asked to update your phone’s Adobe Flash Player, which is, in fact, a virus in disguise, according to the security company.
Here’s how these text messages actually look like:
“Once downloaded, the TangleBot malware can do a ton of different things,” said Ryan Kalember, executive vice president of cybersecurity at ProofPoint. “It can access your microphone, it can access your camera, it can access SMS, it can access your call logs, your internet, your GPS, so it knows where you are,” he continued.
In addition to harvesting sensitive information, the malware is designed to control device interaction with banking apps using overlay screens and steal account credentials. The malware has been in active use for weeks and could potentially harm millions of users countrywide. However, Android does warn its users before installing any software from “unknown software” and displays a series of warning/ permission boxes before the phone is hacked. You can also download third-party security and privacy tools in Canada to ensure maximum security against malware.
“What is making TangleBot fairly interesting right now is that they are using incredibly fresh lures that all map to the sorts of things that we’re hearing about in the news with coronavirus, whether we are talking about the booster or other things that you’re likely to see on the front page of whatever news site you go to,” Kalember explained.
Kalember said that the TangleBot malware displays the compromised users an “overlay” screen that seems legit but is actually a phony window being operated by hackers to steal information. Moreover, TangleBot is also capable of granting itself permissions of access to sensitive device features like call logs, internet, camera, SMS, microphone, and GPS. As a result, enabling hackers to have complete control over the device and turning it into full-blown spyware.
Considering the rising trend of SMS smishing among cybercriminals, users should refrain from responding to unsolicited commercial messages and be careful about providing their number to any commercial entities. The security agency also recommended users not to click any link in commercial messages and watch out especially for those that have a threat warning.
Kalember clarified that the discovery is not actually a vulnerability of Android and his team is in contact with Google for possible mitigation. “This is exploiting the user’s vulnerability. You are basically being tricked into installing the attacker’s code,” said Kalember.