Don’t get reeled in!
As part of our Cybersecurity Awareness Month (CAM) in Canada campaign, as always CanadaVPNs aims to educate our readers about phishing scams and their prevention. With our theme called “don’t take the bait, keep your cybersecurity up-to-date,” we intend to raise awareness regarding various types of phishing attacks, including their identification and what a person can do for their prevention.
What is Phishing?
Phishing is a common internet scam that uses technology to lure users into divulging private information. It mostly involves using deceptive emails and web links that are designed to redirect users to fraudulent websites and trick them into entering their sensitive information like credentials. Hackers also use malware infiltration to steal credentials directly from the target’s device.
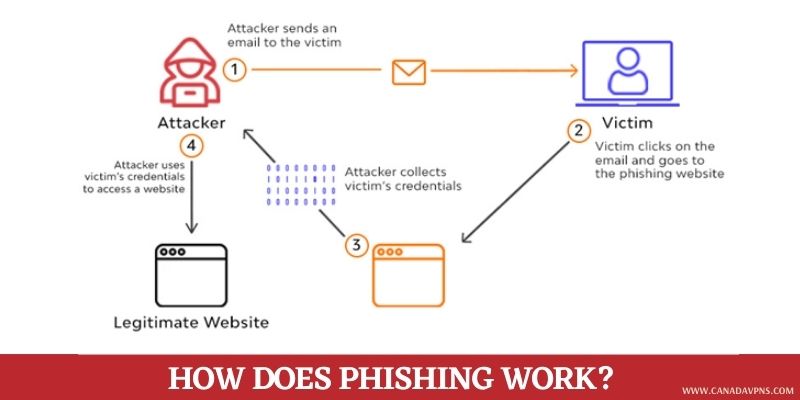
How does Phishing Work?
Before we dive into the conclusion, let’s first discuss how Phishing works. Scammers usually follow a predefined pattern:
What are the types of Phishing attacks?
You may likely experience phishing in the following forms:
- Domain Spoofing: It mimics valid email addresses. These scams may take an original company’s domain (e.g., @netflix.com) and alter it a little bit (e.g., @nétflix) to scam you.
- Phishing Email: This usually lands in your email inbox and asks for your credentials, payment details, email verification, and opens an attachment. These emails are designed in a way to look legitimate or closely resemble a valid one.
- SMS Phishing (Smishing): This tactic will imitate a legitimate organization, using a text message to fool you. These scam messages contain links or phone numbers that they want you to engage with.
- Voice Phishing (Vishing): In this scam, cybercriminals impersonate a valid person or company and call you to deceive you. They keep you on the phone for hours or trick you into taking action.
- Clone Phishing: These scams involve duplicating a real message, with valid attachments and links replaced with malicious ones. It also lands in your inbox or sometimes in the social or promotion section.
- Social media Phishing: Scammers use posts or direct messages to lure you into a trap. Some are from sketchy official organization pages with an urgent request, while others include free giveaway lures. It may also act as a friendly stranger trying to build a relationship with you.
How to Spot a Phishing Scam?
One of the reasons why phishing emails are so evil – and sadly often successful – is because they are designed to look legitimate. Generally, you can identify a phishing email through the following indicators:
- Poor grammar
- Spelling errors
- Irregular structure/fonts
- Lousy graphics
- Dubious attachments or links
- Generic greetings like “Dear Customer” or “Dear User” instead of your name.
- Pointless urgency to enter your details or verify your email address.
Hackers are usually in a rush while creating phishing websites, so some are prominently different from the original ones. This makes it easier to sniff them out of your inbox.
Fear, Lust, Greed: surefire lures of Phishing
Many phishing emails and texts often contain a story to lure you into clicking a link or downloading an attachment. Generally, these include emotionally-driven messages, targeting emotions like fear, greed, and lust to persuade us into falling into their trap. They may:
- Ask you to verify your email or update your payment details.
- Claim they have noticed something unusual activity or log-in attempts.
- May include a fake invoice
- Ask you to click on the link to make a purchase.
- Claim to be a government-generated email, offering you a refund or something.
- Offer a coupon or free stuff
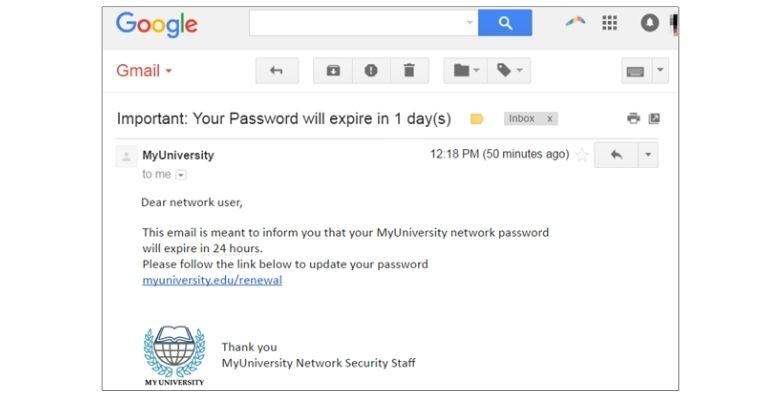
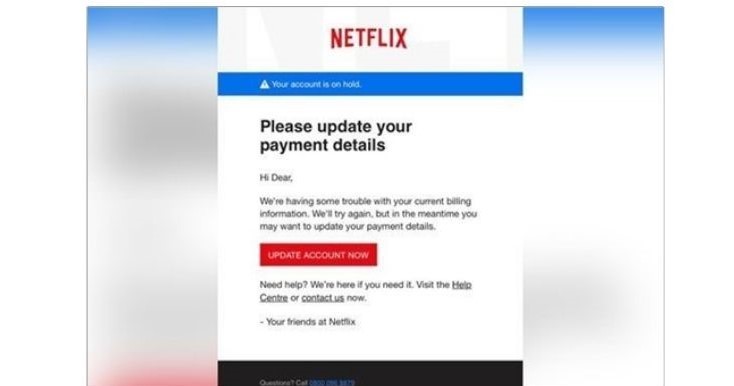
Have a look at these examples of how a phishing email looks like:
Example 1:
Example 2:
How to Shield Yourself from Phishing?
Some email services automatically filter many phishing emails out of your inbox. But hackers are getting smarter, and they have invented new ways to outsmart these spam filters. This means you need to keep your eyes and brain open while clicking on any suspicious email. Here are five steps to protect yourself from phishing:
Five Ways to Protect Yourself from Phishing
Dos:
- Protect your device by using security software: Such online security software and tools are designed to detect and deal with new security threats automatically. Virtual Private Networks are the most efficient way to keep users’ identities private and secure over the internet and thus prevent many cyberattacks on them. You can also install a premium VPN that directly protects you from phishing by encrypting your online traffic.
- Protect your social accounts by using multi-factor authentication: You can protect your social accounts by setting them to Multi-Factor Authentication (MFA). It is an effective security method that requires users to enter two or more credentials to access their accounts. This method is effective because users have to identify themselves with more than just a password or ID. While your credentials might be vulnerable to brute phishing attacks and can be stolen by hackers, employing an effective MFA factor such as a thumbprint or external hardware key can ensure maximum security from cybercriminals. Take a look at the following MFA you can employ on your accounts/devices:
- A security key, pattern, or numerical number
- A scan of your fingerprint, retina, or your face
- Secure your data by backing it up: Back up your data and ensure those backups aren’t connected to your home Wi-Fi. It’s better to make copies and store them in your external drive or cloud storage.
- Keep your Operating System up-to-date: Outdated OS and software are common targets of phishing. Hence, it’s important to keep your software and OS up-to-date. It will be easier to set your system on automatic update.
- Deploy a web filter to block malicious websites: Almost all premium VPN services offer browser extensions to help block websites containing malicious content. You can also install anti-malware software or DNS-protected services for this purpose.
Don’ts:
- Avoid clicking embedded links
- Never trust urgency or alarming messages
- Avoid clicking on the pop-ups
- Refrain from using public Wi-Fi
- Don’t open attachments from a doubtful source
Phishing Attacks have increased Worldwide in the Pandemic
According to the latest report by the non-Profit Anti-Phishing Working Group, online phishing attacks targeting webmail and other cloud-based online services have seen a massive surge since the beginning of the COVID-19 pandemic. As the pandemic tightened its grip worldwide last year, many employees were forced to transition their work operations online. These remote employees are, in fact, regarded as the most vulnerable group to phishing scams by cyber experts.
As per the latest APWG report, around 571,764 unique phishing websites were discovered from July to September. And in the third quarter of 2020, around 1,558 brands were attacked by hackers using phishing scams, out of which 367,287 were subjected to email phishing.
Around 70% of Phishing Attacks are directed towards Canada
The Great White North has been a frequent target of phishing attacks for some years. In fact, the country has been plagued by various phishing scams for the fifth quarter in a row, making it the most frequently attacked country by far, recording 66% of all attacks, according to RSA’s 2020 fraud report. The next in line is the USA, the second most frequently targeted country, accounting for only 7% of phishing attacks.
Now the question arises: Why Canada, though?
David Masson, director of the cybersecurity firm Darktrace, highlighted a couple of possibilities about frequent phishing attacks on Canada. First, we are neighbors to the US and the next big English-speaking nation, making it easier for the criminals to write attacks in English and fool people into assuming them as legitimate.
Another reason is that we have the biggest economy. “We are a rich country,” Masson said, referring to the country’s massive SMB market, successful startup/freelancer community, and the talent that’s nurtured within it. Plus, Canada stands at the top 10 counties with maximum per-capita income for several years and leads the G7 in economic growth. With this amount of money in our pocket, hackers deem Canadians as their favorite targets.
Canadians overestimate their ability to Sniff Out Phishing Attacks
According to the survey conducted by the Canadian Bankers Association, over 7,800 Canadians (80%) across five demographic groups sought to be “confident” in their ability to identify and respond to phishing attacks. But despite that, only 31 percent were able to spot all the red flags of a phishing scam correctly. Furthermore, the results suggest that more than half (57%) of the respondents assume that phishing emails are easy to identify due to spelling errors, suggesting a general lack of understanding of the increasing cleverness in phishing scams.
Just recently, hackers were found to be using a new kind of malware, “TangleBot”, with COVID-19 lures to target users in Canada. They are using SMS phishing malware as part of the COVID-19 awareness campaign to fool users into clicking infected links so they can steal their credentials or other financial information.
In a Nutshell
Think twice before you click on anything! You may find yourself browsing through emails, mindlessly clicking links without even properly reading the message. While doing so, you may stumble upon a cunningly crafted mail that finds its way to your inbox rather than the spam folder.
Therefore, it’s important to think twice before clicking any embedded links, especially when it comes from an unknown source. Phishing attacks are getting prevalent in Canada, a combination of user awareness and robust security is paramount. Since human limitations can lead to mishaps and failure, we need assistance from non-human entities – like security tools and software – that are immune to errors.