Security Alert! Your information might be at risk on Ford’s website!
Ford, a popular car manufacturing company, has a bug on its official website that allows security researchers access to confidential information, including the company’s employee records, internal tickets, consumer databases, and much more.
Security researchers Roberts Wills and break3r were the first ones who discovered the glitch on the company’s website before bringing it to the attention of Sakura Samurai members, an ethical hacking group.
Tracked as CVE-2021-27653, the bug that caused this vulnerability is itself information visibility originated from wrongly configured instances of Pega Infinity running on Ford’s hosting servers.
To exploit the loophole, an attacker would first need access to the back-end web panel of a wrongly configured instance of Pega Chat Access Group portal.
“The impact was massive. An attacker could exploit a vulnerability identified in a broken access control to steal a pile of sensitive records, perform account hijacking, and obtain large amounts of data. There is,” said Rober Mills while sharing his insights on the incident.
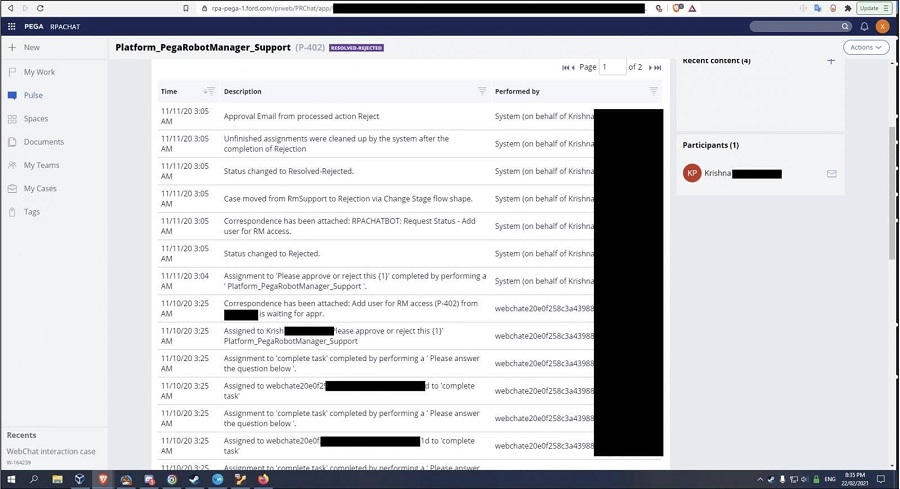
Researchers also shared some screenshots of Ford’s confidential information on their internal system. You can see the company’s ticketing system in the screenshot below:
Vulnerability exposed and Ford’s response
While the magnitude of the vulnerability is quite massive, the company doesn’t seem to care much…
Now, anyone in that position would go all panicky like calling an emergency meeting, subscribing to VPN services for online security, getting engineers on board, and trying to fix the bug as soon as possible. But this wasn’t the case with the giant automobile manufacturer!
Although the company did address the vulnerability in their chat portal, it wasn’t that cooperative in the beginning when the issue was brought to their knowledge by Sakura Samurai members via its HackerOne vulnerability disclosure program.
The member of Sakura Samurai explained in an email that the company even stopped answering their emails at one point. In fact, HackerOne had to announce the glitch and its potential disaster on social media to get an initial response from the company – they didn’t release any sensitive information back then.
At last, after six months of waiting though, the researchers had to disclose the vulnerability on their own due to HackerOne’s policy. It’s important to note that the security researchers didn’t receive any monetary incentive for disclosing the vulnerability to the public. Instead, they did this for the sake of concerns for the company’s customers.
As of now, it’s not known whether someone has tried to exploit the glitch and gained access to sensitive information. Now that the information is out there for grabs, someone somewhere will most likely… But we hope not!