As the world becomes more and more interconnected each day, it has become necessary to stay safe & secure online. Privacy and Security both are two different concepts and much bigger concerns these days. From a security and privacy point of view, the safest browser offers a range of robust data-protection features and makes them simple to use. In this article we are discussing Tor browser benefits and complexities. It would not track your online activity, and it would prevent anyone from laying their hands on your data and information.
What is TOR?
“TOR” is an acronym for “The Onion Router.” The name comes from its uncanny relation to the onion and anyone who has ever cut into an onion knows that it’s made up of many layers. We will get to the layers part later on. Tor is a widely acknowledged software with its own internet browser. Using the Tor network, the Tor browser anonymizes your web traffic and thus making it easy to protect your identity online.
But how did this technology emerge onto the scene? In early 1955, the US Navy was looking for ways to securely communicate their sensitive intelligence information. Officials from the Naval Research Lab, including a mathematician and two computer scientists then came up with something called “onion routing.”
It was introduced as a new technology that would protect your internet traffic with different layers of privacy. Although this new network technology was initially utilized for military services, by 2003 Tor was in the hands of the public and has since then continued to grow.
Tor browser Benefits and Complexities- Quick Review
Three primary uses of Tor are the following:
-
- Bypass censorship and surveillance
- Visiting websites anonymously
- Accessing Tor hidden services (.onion sites)
Let’s take a brief look at the things we like about tor and the things that we don’t before digging further into each aspect.
| PROS | CONS |
| Exceptional anonymity | Slow compare to VPNs |
| Tor provides 3 layer proxy | It’s possible to de-anonymize your browsing by making a simple mistake |
| Your real IP address cannot be determined | Illegal in some countries |
| You can access websites without your internet provider being aware | Websites may refuse to function when you’re using Tor |
| You can bypass many kinds of censorship | |
| You can host websites that are only accessible by other Tor users | |
| You can get access geo-restricted content |
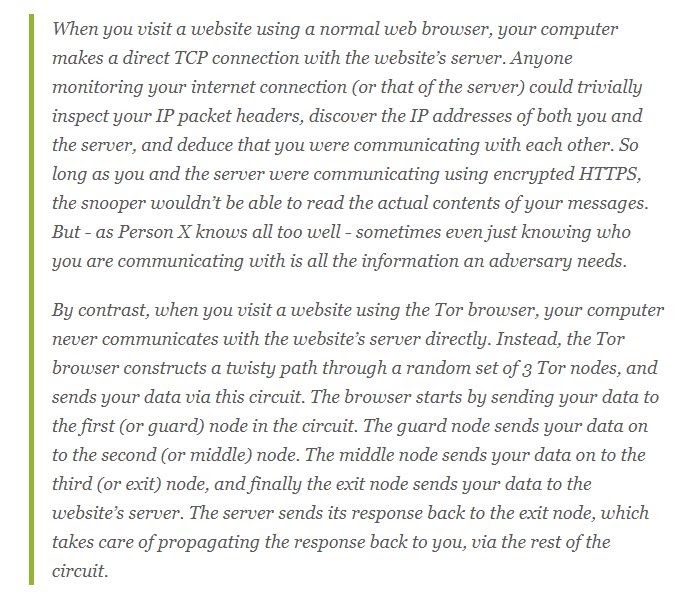
The TOR Network
At first glance, the science around Tor may seem daunting and alien. Don’t worry though. It’s simpler than it seems. Starting from the very basic level, once you connect to the internet with your Tor browser, your internet traffic is stripped of its first layer of identifying information as it enters the Tor network and is then sent bouncing through different relay nodes, which then encrypts and privatize your data, layer by layer, like an onion. Finally, your traffic arrives at the exit node and leaves the Tor network for the open web.
Once you’re in the Tor network, it’s nearly impossible for others to track your traffic’s footprints worldwide. And once you leave the Tor network via an exit node, the website you view isn’t sure which part of the world you’re hailing from, offering you more privacy and protection.
Software engineer Robert Heaton has a great summary of how tor keeps you anonymous:
How to browse with Tor
Browsing with Tor is just like browsing with any other web browser normally. Once you download the free browser from the official website follow the installation instructions and set up the browser. When you open Tor for the first time, it will ask you to configure your connection. This may take a few minutes to find a set of relays to connect you through. But once you’re in, you can use Tor just as you would use chrome or Firefox.
Once you start browsing, the first thing you’ll notice is that it’s slow or at least, slower than regular internet browsing. Since your data is going to jump through a lot of relays, your experience on Tor might be more sluggish than your normal internet browsing. This becomes quite noticeable if you try to watch Netflix or make voice-over-IP phone calls or video calls with Zoom. This is mainly because Tor technology isn’t necessarily built to provide smooth audio-video experiences. Still, Tor has gotten quite faster over the years, and with a good internet connection, you can even watch YouTube videos.
Tor Browser gives you access to websites that are only available within the Tor network, these are the addresses that end in .onion. This makes it possible to read the news anonymously, a feature that is desirable in a country where you don’t want the government knowing which news sites you’re reading.
Tor’s Security & Anonymity
Tor is useful for anyone who wants to keep their online activities out of the hands of advertisers, ISPs, and websites. This also includes people getting around censorship restrictions in their country, people looking to hide their IP address or anyone else who doesn’t want their browsing habits being observed.
So clearly Tor sounds perfect on paper but there are plenty of ways your security and anonymity might be compromised using tor. For example, consider this scenario from Naked Security’s Paul Ducklin:
That’s not all. Many of the ways you’d use a normal web browser could also leave some breadcrumbs for a curious onlooker to easily figure out who you are. As the Tor Project describes:
The Dark side of Tor
While all of these anonymity details might seem very positive and useful, not everyone uses Tor in all the right ways. For example, many hackers and cybercriminals use it to stay anonymous while managing their illegal business. This anonymous browser is especially useful to criminals because it provides access to the dark web. All hidden service domain names that end in .onion are sometimes referred to as the dark web.
But let’s just not put all the blame on Tor. While it’s true that some criminals use Tor to commit crimes, anonymity online is not merely the concern of criminals. There are plenty of perfectly legitimate uses for Tor’s hidden services.
Websites like Facebook, DuckDuckGo, and The New York Times run versions of their sites with .onion addresses for journalists and activists living under oppressive regimes.
Likewise, journalists use Tor to protect their sources they do not want to risk being revealed. Many people use it to access the content inaccessible in their region and bypass censorship to view the content.
Will Tor work with a VPN?
Yes, in most cases it will. However, it takes some proficiency to be able to configure your VPN connection to work in harmony with Tor. A successful combination of the two can be very useful while you browse anonymously with Tor.
Although using tor already provides sufficient safety and anonymity to your online traffic but such is not the case with applications that run outside your browser as these will not be protected by the Tor network. If you want to make sure all your online activity is encrypted and anonymized, a VPN combination might be a better solution.
Advantages of VPNs over Tor include much better connection speeds for downloading videos and other large files. With a VPN you can choose the server your data is routed through and finally, it is far easier to use a VPN system-wide than it is to use Tor outside of Tor Browser.
There are, however, also some things a VPN can’t do. Like it won’t give you access to the dark web, first of all. The second advantage of Tor over VPNs is that the browser is completely free. On the contrary, most good VPNs come with monthly subscription packages and are definitely not free.
TOR on Mobile
Today more and more people are browsing the web from their mobile phones since it’s a more portable way to go online. As a result, the Tor Project has spent a couple of years working to set up a better Tor Browser for mobile phone users.
In September 2019, the Tor Project announced the official release of Tor Browser for Android. The Tor Project has not yet released an official Tor Browser for iPhone and iPad users, but endorses Onion Browser for iOS users who want to browse the web anonymously.
FAQs
Which search engine does Tor use?
strong>Does Tor work in China?
Is using Tor legal?
Does Tor hide my IP?
Conclusion
In conclusion, Tor is a powerful tool that must be used very smartly. The service is free and easy to download but does have its own limitations. So if you’re an average user looking for some dog GIFs and browsing Facebook, you probably don’t need to worry about the government spying on your activity. Using tor would just slow down your connection. It’s more likely that you need to secure your internet rather than anonymize it when you’re using public Wi-Fi.