Uncover the mystery behind complicated acronyms of VPN protocols!
There seems to be a new reason to get worried about your online privacy every day. Data breaches, repressive censorship regulations, exploitations of private data, and so much more. Only if there was some way to reclaim control of our privacy…. Enter: Virtual Private Network (VPN)
VPNs have long been a popular choice for people seeking more privacy in their everyday internet browsing. A VPN works by creating tunnels between your device and a remote VPN server, encrypting all the data that goes through it. These tunnels are formed with different programs and processes called VPN protocols.
However, outdated protocols can be incompetent and may not offer enough security or privacy as the new ones. Bear in mind that there are multiple types of encryption protocols, each of which provides different solutions to internet security, privacy, and anonymous internet browsing.
Therefore, if you use a VPN service, you need to know the various VPN encryption protocols and what they do. Also, it’s important to ensure your provider uses the best and more secure ones. That’s why we’ve compiled this guide to educate you about VPN protocols so you can make an informed decision while purchasing a VPN service.

Quick Summary of VPN Protocols
Running out of time? Here’s a quick guide on the different VPN protocols used by VPN services:
- OpenVPN is a wise choice, especially when the setup is operated by a third-party app.
- L2TP/IPSec is the oldest and the most prevalently used protocol that provides decent security.
- SSTP is the best for Windows users due to its full integration with every Microsoft operating system.
- IKEv2 is a common VPN protocol that provides secure key exchange sessions.
- PPTP is one of the oldest tunneling protocols and should only be used as the last expedient.
- WireGuard is the latest protocol that is considered to be the fastest and more efficient than the rest. However, it does have some privacy drawbacks
What are VPN Protocols?
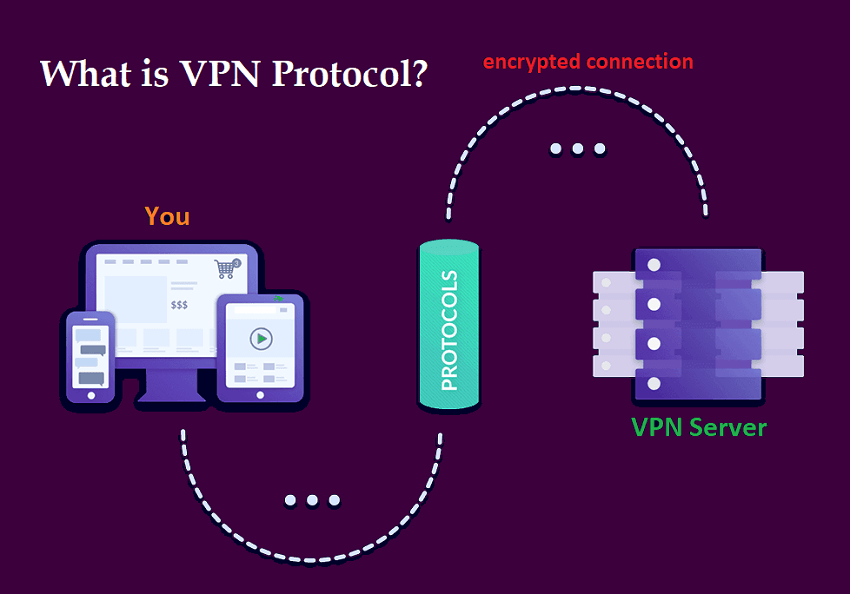
A VPN protocol is a set of programs or rules that dictate how data will be packaged and delivered over a VPN tunnel. These protocols have varied specifications based on the benefits and preferred scenarios. For example, some VPN protocols prioritize security over speed while others focus on quickly transferring data packets for boosting speed. But they more or less perform the same function:
- Establish a secure tunnel for your data to reach the remote server. This way, your connection remains private and end-to-end encrypted, making your data difficult to intercept.
- Bypass geo-restriction. You can wrap your traffic in the TCP or UDP protocols, bypassing firewall blocks on various websites by changing your IP address.
Also, note that there are two primary approaches to VPN functionality:
- Two protocols are used (one to transfer the data through the tunnel and the other to secure that traffic)
- One protocol is used for both transferring and securing the data.
Just to be clear, no VPN protocol is perfect. Obviously, there is always room for improvement – Some have security flaws, and others have slow speed. So, let’s delve into each protocol and see which one suits your needs the best:
6 Common VPN Protocols
Check out these six common VPN protocols and their pros and cons:
1. OpenVPN
Wondering what is OpenVPN? OpenVPN is an open-source protocol used by many VPN providers. It allows developers to access its underlying code and runs on either the TCP or UDP internet protocol. The combination of these two protocols ensures that your data will be delivered in the right order with fast speeds.
This protocol is also known for its use of AES-256-bit key encryption with 2048-bit RSA authentication along with a 160-bit SHA1 hash algorithm.
Pros:
- Open-source – the protocol is transparent, which means developers have access to verify the code for hidden backdoors or vulnerabilities that might compromise your security.
- Security – With its military-grade encryption, your data will be secure and hidden from the prying eyes.
- Versatility – this protocol can be fused with various encryption and traffic protocols, programmed for different purposes, or be as secure or fast as you want it to be.
- Bypasses most firewalls. With the OpenVPN security protocol, you will easily bypass the Firewall.
Cons:
- Confusing setup. While it has a versatile configuration setup, most users may get confused or petrified by the complexity of setting up their own OpenVPN. However, many VPN providers make it easier to install and run this protocol without any manual configuration, as it has been taken care of by the provider itself.
When can OpenVPN be used?
OpenVPN is the wise choice when you need an extra layer of security while carrying out day-to-day browsing activities like connecting to public Wi-Fi, accessing sensitive information, or using financial accounts.
2. L2TP/IPSec
Layer 2 Tunnel Protocol is usually combined with IPSec for security. L2TP was jointly developed by Microsoft and Cisco in the 90s. So, it’s relatively older than OpenVPN and does not provide any encryption or privacy. But when it is fused with security protocols like IPSec, it becomes extremely secure and has no known vulnerabilities.
Pros:
- Security. The fact that L2TP does not offer any security makes it extremely secure. Confused? Well, that’s because it can support multiple encryption protocols designed for security, making it secure and light-weighted.
- Widespread availability – L2TP is compatible with almost all new operating systems, allowing users to configure it and get it running without any trouble.
Cons:
- It relies on other protocols.
- It can potentially be compromised by the NSA.
- Slow – It encapsulated data twice, resulting in slower speed and connectivity than other protocols.
- Has difficulties bypassing firewalls – users who configure L2TP can face difficulties bypassing firewalls used by surveillance-oriented system administrators.
When can L2TP/IPSec be used?
You can use L2TP when shopping online or performing banking operations. It is also secure when you combine several company branches into one network.
3. SSTP
Developed by Microsoft, Secure Socket Tunneling Protocol (SSTP) has fully integrated every Microsoft operating system since Windows Vista SP 1. It uses 256-bit SSL keys for encryption and 2048-bit SSL/TLS certificates for authentication. Despite being primarily designed for Windows OS, the protocol is also available to other devices.
Pros:
- It’s good for Windows users. Since Microsoft owns and develops the protocol, SSTP is well supported by your Windows OS or built-in. This means that even if you try to configure it manually, the process will be easier, and you can even get Microsoft support.
- Secure: It uses AES-256 encryption protocol, similar to other leading VPNs.
- Bypasses firewalls – SSTP can easily bypass most firewalls without delaying your communications. It is also effective in unblocking geo-restrictions on various streaming sites like HBO Max in Canada.
Cons:
- The biggest drawback to STTP is that it’s a Microsoft-developed entity, and other developers don’t have access to its underlying code. In addition, this protocol is suspected of having backdoors since Microsoft itself has been known to cooperate with the NSA and other law-enforcement agencies. And for the same reason, many top VPN providers avoid using this protocol.
When can SSTP be used?
This VPN protocol is best for bypassing geo-restrictions and enhancing privacy while browsing the internet.
4. IKEv2
Internet Key Exchange version 2 is a commonly used VPN tunneling protocol that offers a secure key exchange session. Like L2TP (and IKEv1), – is usually paired with IPSec for authentication and encryption.
Pros
- Stability: When fused with the IPSec tool called the Mobility and Multihoming Protocol, it ensures a stable VPN connection when you switch between network connections. This makes this protocol more dependable and stable for mobile devices.
- Speed: It utilizes a little bandwidth when active, and its NAT traversal makes it faster to connect and communicate. It also helps to bypass geo-restrictions.
- Security: IKEv2 utilizes leading encryption algorithms, providing users with military-grade encryption.
Cons
- Limited Compatibility: IKEv2 doesn’t support all devices. Since Microsoft helped create this protocol, there won’t be a problem for Windows users. But some other updated Operating Systems will require to go with the updated versions.
When can IKEv2 be used?
IKEv2 is good at re-establishing the link after a temporary connection loss and efficiently switching connections across network types (from Wi-Fi to cellular data, for example).
5. PPTP
Point-to-Point Tunneling Protocol (PPTP) is one of Microsoft’s oldest VPN protocols, created in the mid-90s. This protocol was incorporated into Windows 95 and particularly designed for dial-up connections. But with the advancement of technology, PPTP VPN’s basic encryption becomes inefficient and can quickly be compromised. Since it lacks many of the security features found in the latest protocols, it can deliver the fastest connection speeds for users who may not need heavy security. In fact, this protocol is still being used in some applications, but most providers have since upgraded to faster and more secure protocols.
Pros
- Fast – Since the protocol doesn’t really care about the security measurements, it delivers fast connection speeds.
- Widespread compatibility – Point to Point VPN protocol is compatible with almost all major Operating Systems.
Cons
- Insecure – it has several vulnerabilities and security issues. Some may have been patched, but it is still susceptible to breach and other cyber attacks. Even Microsoft itself encouraged users to switch to SSTP or L2TP.
- Blocked by Firewall – its outdated encryption techniques make it easier for Firewall to block the access upon detection.
When can PPTP be used?
You can use the PPTP VPN only for streaming. Other than that, you should go for a more advanced VPN protocol option.
6. WireGuard
WireGuard is the latest and fastest tunneling protocol in the VPN industry to date. It utilizes ultra-modern cryptography that outclasses the existing leaders – IPsec/IKEv2 and OpenVPN protocol. However, this protocol is still in the experimental stage, so VPN providers have to look for other protocols to overcome WireGuard’s shortcomings.
Pros
- Advanced and extremely fast – It is the “leanest” protocol in the list, consisting of only 4,000 lines. However, OpenVPN has 100 times more lines than WireGuard.
- Free and Open Source VPN server– Anyone can look into this protocol to verify any back doors. This makes it easier for developers to audit, deploy and debug.
Cons
- Experimental stage – Despite being the fastest protocol, WireGuard is still under experimentation. It fails to provide complete anonymity and has many other issues. If these issues are addressed soon, it could become the “next big thing” in the VPN industry.
When can WireGuard be used?
With WireGuard’s fast speed and connectivity, this protocol is mostly used by Netflix VPNs, reliable VPNs for gaming, VPNs for torrenting, or can be used for downloading larger files.
VPN Protocols Comparison Table
Here is a quick roundup of all the above-explained VPN Protocols;
|
VPN Protocols |
Speed | Encryption | P2P | Stability |
Streaming |
|
OpenVPN |
Fast | Excellent | Good | Good | Good |
|
L2tp/IPSec |
Average | Average | Poor | Good |
Poor |
|
SSTP |
Average | Good | Good | Average |
Average |
|
IKEv2 |
Fast | Good | Good | Excellent |
Good |
|
PPTP |
Fast | Poor | Poor | Good |
Poor |
| WireGuard | Very Fast | Excellent | Good | Excellent |
Good |
FAQs
Which VPN protocol is the best?
What is the fastest VPN protocol?
Which VPN protocol is the most secure?
What is the most stable VPN protocol?
Which VPN protocol is the best for torrenting?
Which VPN protocol is the easiest to set up?
Conclusion
If you set out to purchase a VPN service for yourself, you need to know what type of VPN protocols they offer. Since all VPN protocols are designed for different purposes, it is important to consider what you need from a VPN connection.